AN EVENT FOR HACKERS TO COLLABORATE RESEARCH LEARN GROW
Vendors Researched at Past Events
LATEST RESEARCH ARTICLES
Evilginx Directory Traversal and IP Blacklist Bypass Exploit
We identified a Directory Traversal and IP Blacklist Bypass vulnerability that has been in Evilginx2 for 2 years …
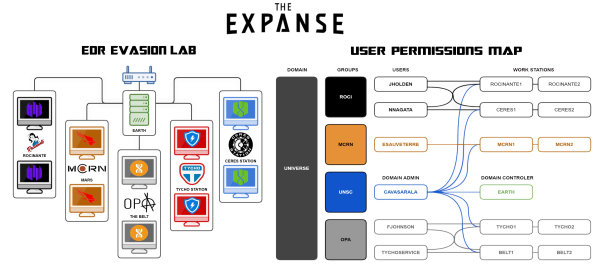
EDR Evasion Results
We are currently working to convert all the old writeups/articles into the new format …
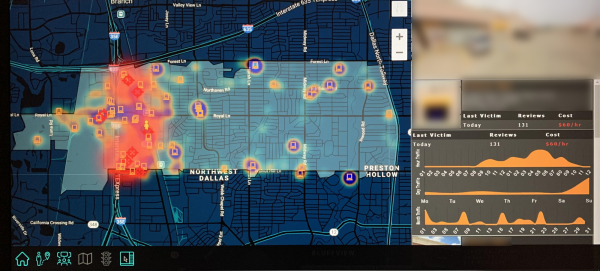
Tactical Data Analytics
We are currently working to convert all the old writeups/articles into the new format …